Featured Stories
See allAngular Signal Forms Series: Getting Started with Signal Forms
With the release of Angular 21 on Nov 20, Angular introduced the long-awaited Signal Forms, providing scalable, composable, and reactive forms built on Signals. Although Signal Forms are still experimental, let's take an initial look at them. Instead of building forms from scratch, you start with your data model and let Angular generate the form structure automatically.

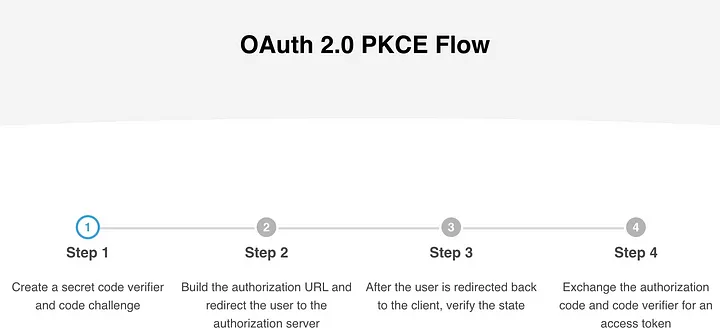
Enhancing OAuth 2.0 Security with PKCE: A Deep Dive into External Partner Integration
In the modern digital landscape, security is paramount, especially when dealing with third-party integrations that require authentication and authorization. OAuth 2.0 is widely adopted as a secure authorization framework, but traditional flows, such as the implicit flow, have proven vulnerable to security risks like token interception. To mitigate these risks, the Proof Key for Code Exchange (PKCE) extension was introduced, enhancing OAuth security by ensuring that authorization requests and token exchanges originate from the same client.
Latest Stories
Angular Signal Forms Series: Key Features of Signal Forms
Angular introduced the long-awaited Signal Forms in v21. Let's take a look at the new features and how to achieve real-world cases like complex validators, nested forms, and custom form controls.
Angular Signal Forms Series: Getting Started with Signal Forms
With the release of Angular 21 on Nov 20, Angular introduced the long-awaited Signal Forms, providing scalable, composable, and reactive forms built on Signals. Although Signal Forms are still experimental, let's take an initial look at them. Instead of building forms from scratch, you start with your data model and let Angular generate the form structure automatically.

Debugging a Memory Leak in a .NET Framework Windows Service
A few months back, our team observed a memory leak in Windows service while performance testing our APIs with burst load of HTTP requests. The issue was caught and fixed in time, as its impact was critical to our resource consumption. The following post covers our journey in reproducing the memory leak at fault, as well as our analysis of the dump file using diagnostic tools and our eventual fix that resolved the problem. I’ll finish with key takeaways from this journey.
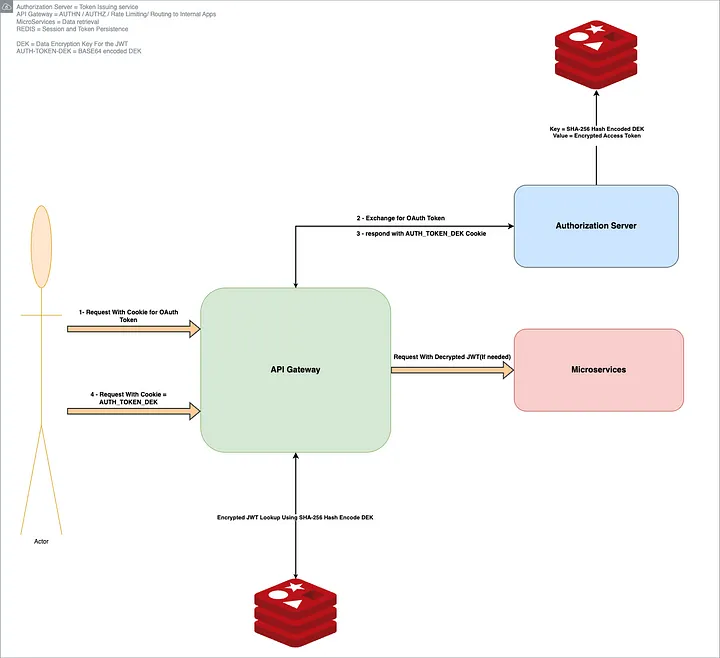
Taming the Oversized OAuth2 Token: A First-Hand Tale from a BFF Architecture
I vividly recall how a seemingly insignificant detail ended up disrupting our entire authentication flow. As an engineer at Omnissa Intelligence (OI), I was on the front line when our frontend-heavy application (with a Backend-for-Frontend (BFF) API Gateway) started mysteriously failing to authenticate certain users. We’d see login attempts succeed, only for users to be immediately logged out or stuck in reload loops. Diving into logs and browser data, we discovered the culprit: an OAuth2 JWT access token so large that it exceeded browser cookie limits, causing the cookie to be silently dropped. This is the story of how we diagnosed the “giant token” problem, learned from industry insights, and engineered a robust solution using envelope encryption to regain control of our sessions.
Proactive Bug Hunting and Error Monitoring with Sentry
We don't live in a perfect world, and software is no exception to that. Testing can't always catch everything or anticipate every potential failure with third-party dependencies or services. Code reviewers and the engineers who wrote the code are susceptible to fatigue and human error. It is simply a fact that bugs and other errors are going to happen at some point. Acknowledging this truth requires that we have feedback mechanisms in place to let us know when unexpected errors occur, so that we can quickly investigate and resolve issues before they impact our customers. It's even better (and much less expensive) when issues are detected before they can even reach our customers.

Enhancing OAuth 2.0 Security with PKCE: A Deep Dive into External Partner Integration
In the modern digital landscape, security is paramount, especially when dealing with third-party integrations that require authentication and authorization. OAuth 2.0 is widely adopted as a secure authorization framework, but traditional flows, such as the implicit flow, have proven vulnerable to security risks like token interception. To mitigate these risks, the Proof Key for Code Exchange (PKCE) extension was introduced, enhancing OAuth security by ensuring that authorization requests and token exchanges originate from the same client.

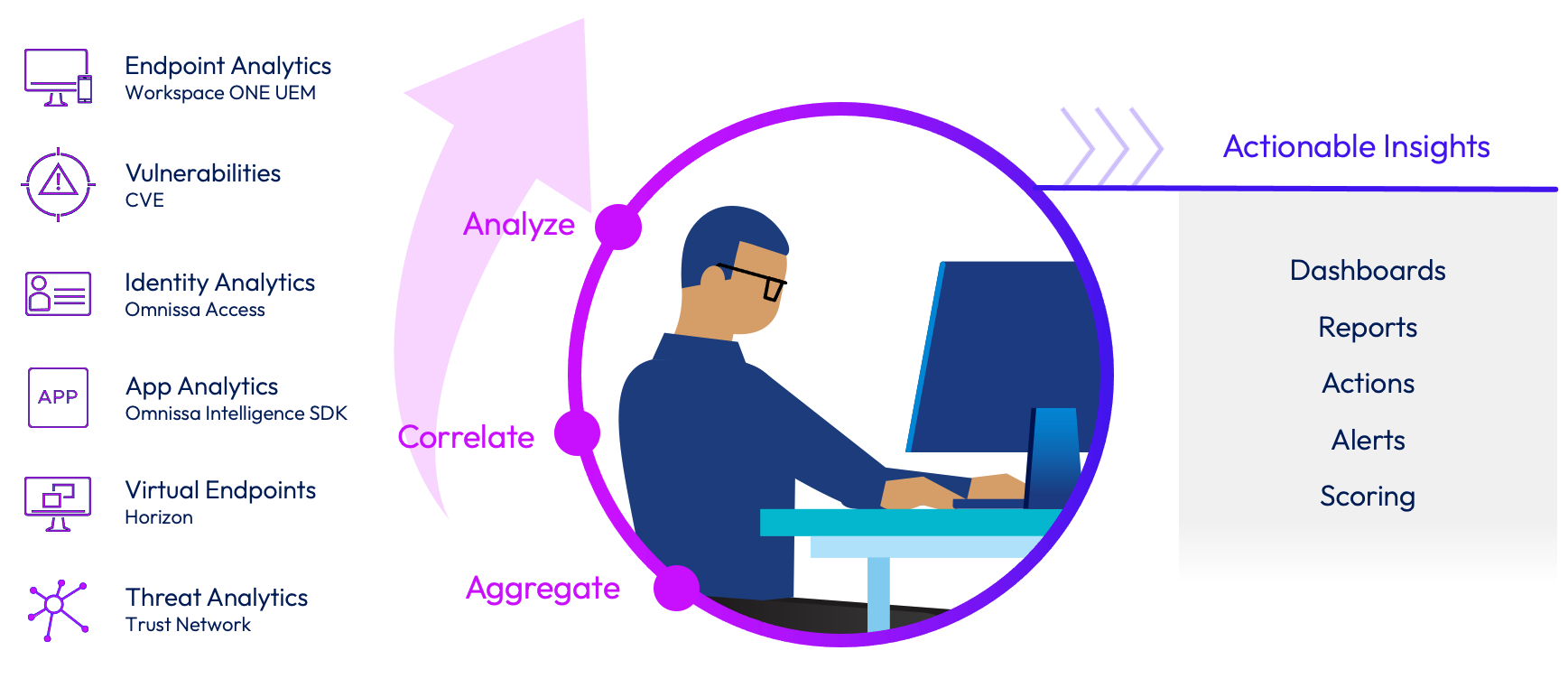
Omnissa Intelligence
Omnissa Intelligence is a cloud-native platform designed to unify and analyze telemetry across digital workspaces, providing actionable insights that drive efficiency, security, and user satisfaction. By aggregating data from various sources — including devices, applications, and user interactions — it enables organizations to monitor digital workspace metrics, proactively identify issues, and automate remediation processes.
First cut: Individual Contributor to Engineering Manager
This is a reflection or retrospection and an attempt to share the takeaways of my journey so far. I started officially as an Engineering Manager in the last 8 months. Before that, I was acting as a Tech Lead, just got promoted to Staff Software Engineer. I have been in the information technology industry for the last 10+ years and one of the things that were pretty clear to me since the beginning was that my personality is more people-oriented and I like to talk to people, engage with them along with spending time on solving technological problems. Few people see moving to a management role as a promotion but I always looked at it as a new role starting from ground zero and thus I need to be mindful of what needs to change in my daily routine/responsibilities going forward. I knew right off the bat that if I don’t change anything then I’ll be shooting myself in the foot. As an individual contributor, I was exposed to only technical problems but on the flip side, I’d be exposed to Products, People, Processes, and Technical Problems (Yes, you read that right!).

New Hire Rules
The other day I bit the hook on an alluring bait article about an outraged dad and a list of rules his 16-year-old daughter had received from her boss the first day on the job. Do tell!
